Network Forensics
6[84]45 Week 5
What is a packet?
- A chunk of data, forming part of a complete payload
- Max packet size is about 64KB
- Usually 1500 bytes (MTU size)
- What happens when you stream a movie?
What’s in a packet
- Packets contain a header and a payload
- Header contains metadata
- e.g. size
- e.g. source
- e.g. destination
- Payload is all the data
- Header contains metadata
- Encapsulated PDUs (Protocol Data Unit)
OSI
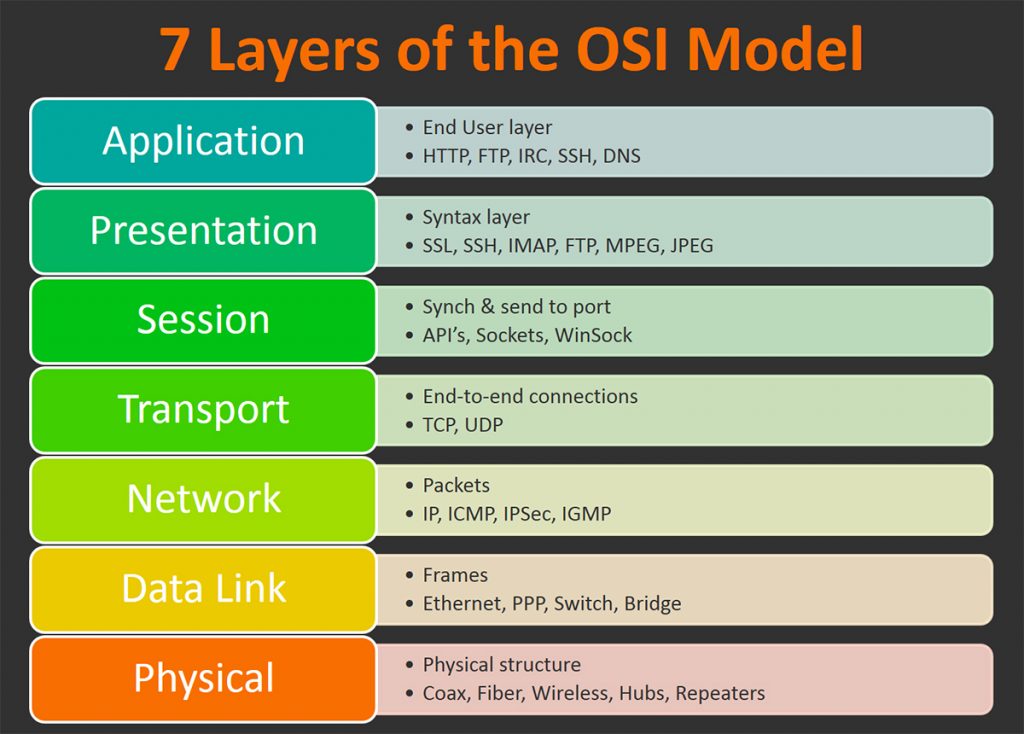
blah blah blah networks.
Routing, hops…
MAC…
IP addresses, DNS, domains, ports…
TCP, UDP…
HTTP, HTTPS, paths, headers…
Packet capture
Intercepting Layer 2 traffic, and storing them into a Packet CAPture file (PCAP)
- Encapsulation
- What about layer 1 traffic?
Demo
Analysing traffic with Wireshark
Display Filters
Conversations
Packets can be tied to a “conversation”
- You can follow them by
- Right clicking a packet >
follow X stream - Filtering for
X.stream eq N
- Right clicking a packet >
Xwould beTCPorUDP
Nwould be a number
Analysing Wireshark traffic
- Who
- What
- When
- Where
Encrypted Traffic
Some traffic will be encrypted (e.g. SSH, HTTPS)… how do we read these?
We need the encryption keys
Encrypted Traffic
If you have them though… e.g. SSLKEYLOGFILE
- Edit > Preferences
- Protocols > TLS
There you can you set the TLS / SSL keys to decrypt the traffic
HTTP/2
Where to perform a packet capture?
- Computers, devices
- Network infrastructure
- literally anywhere™️
Challenges when packet capturing
- Is packet capturing enabled (time)?
- What packets are captured (scope)?
- How many packets are captured (size)?
Packet Routing
Layer 3 - Network - IP address
Layer 2 - Data Link - MAC address
Packets end up traversing across layer 2 networks
- ARP: IP -> MAC resolution
- ARP tables (which switch port has which MAC)
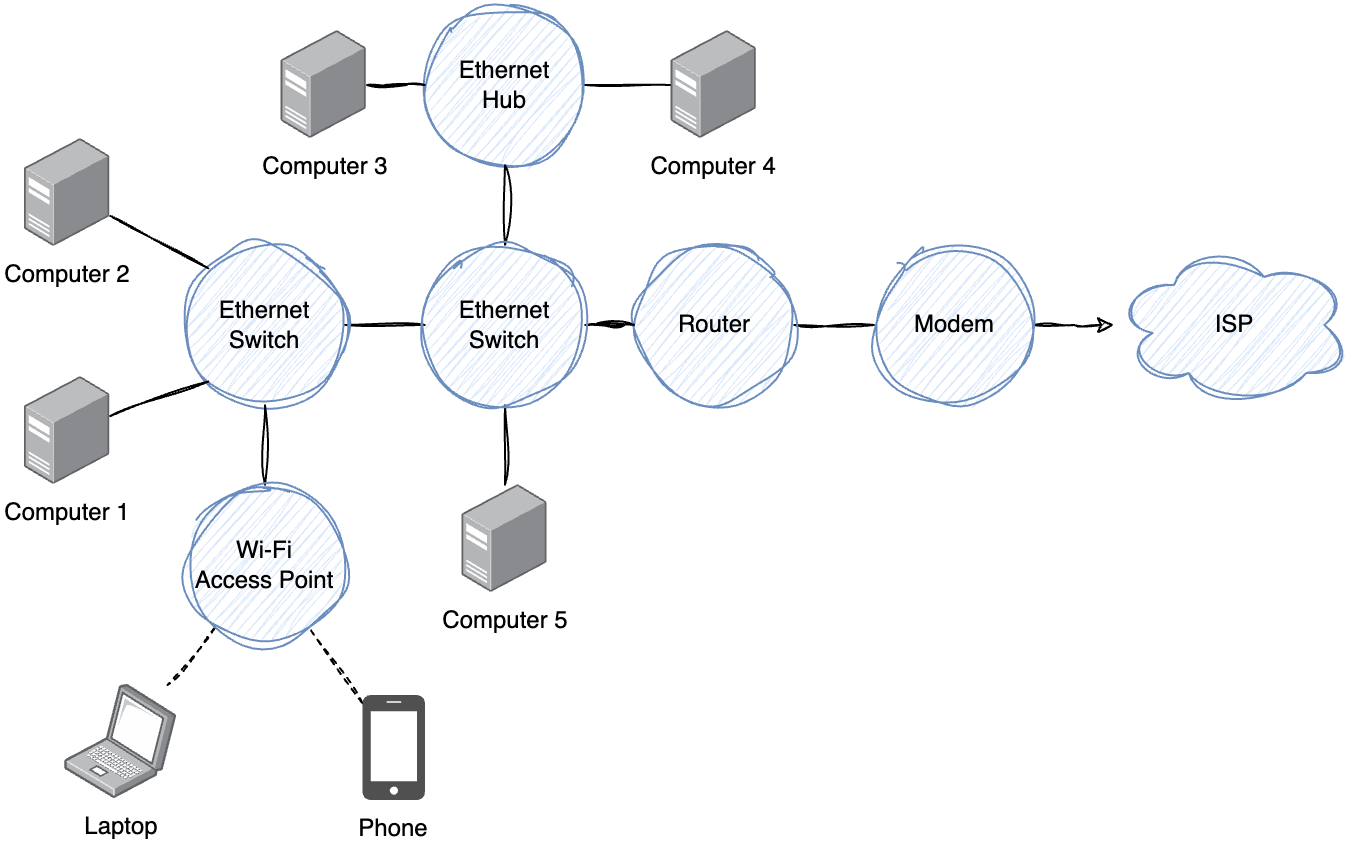
Packets only travel where needed
- Switches do not emit packets on all ports
- Packet capturing on a computer connected a network switch
- Probably won’t see other device traffic..
Summary
It’s important to know where a packet capture was “tapped” from.
- Where should I tap from to
- Capture just my device’s traffic?
- Capture all WAN (internet) traffic from my network
- Capture traffic between two computers
- Capture Wi-Fi traffic?
Legal Implications
Am I allowed to capture packets?
- Do you have permission?
- Workplace monitoring
- Privacy
- Identification
Other Analysis Tools?
- There are some online sites
- But should you be uploading them there?
- TShark (CLI)
- https://github.com/xplico/CapAnalysis
Extended: Cloud Forensics
- Ask your vendor
- Application logs
- Traffic flow logs